Forget printers getting hacked and informing users to subscribe to PewDiePie, its Chromecast’s turn. A couple of mischievous hackers have exploited thousands of Chromecast devices to promote Swedish YouTuber Felix “PewDiePie” Kjellberg’s channel.
The hackers, known as “HackerGiraffe” and “j3ws3r” found a vulnerability in the router settings of smart devices hooked up to televisions. This vulnerability made Chromecasts and Google Homes publicly visible on the Internet.
HackerGiraffe and j3ws3r were able to exploit this to broadcast videos on connected televisions. The hackers had discovered 72,341 exposed devices at the time of writing. The hack is known as “CastHack” and the CastHack website is keeping the Internet updated on its success.
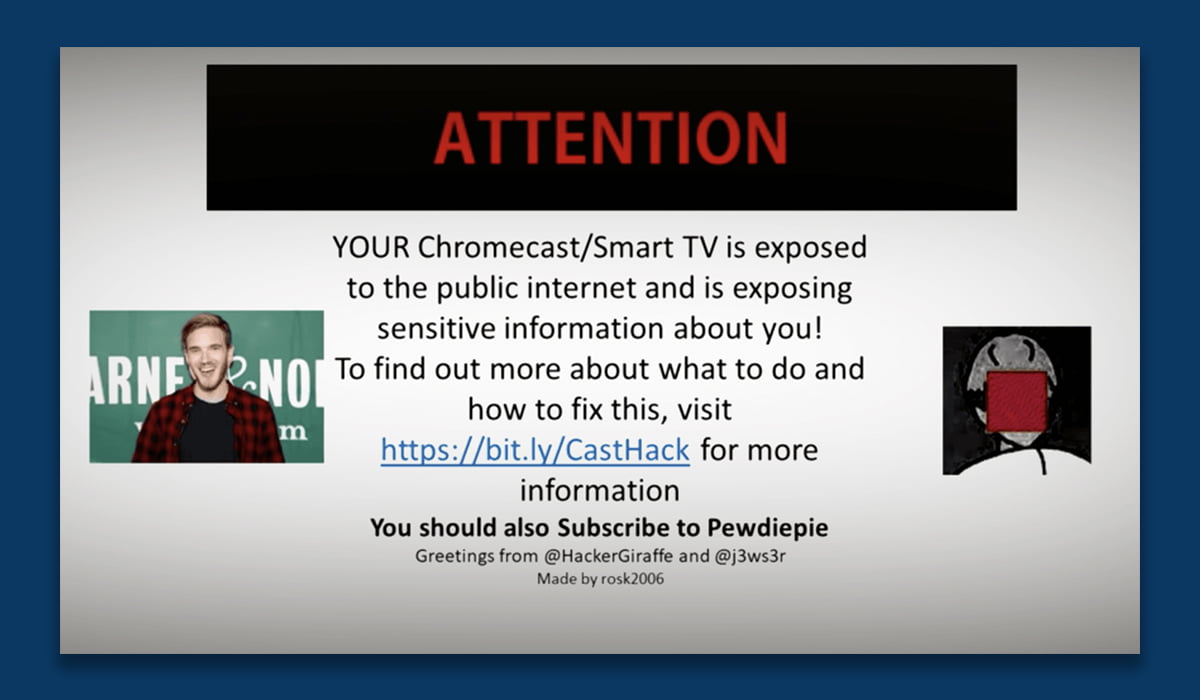
CastHack displays a message instructing viewers to subscribe to PewDiePie and KeemStar, another YouTuber who covers feuds and gossip news. The website also had links to the hackers’ personal Twitter accounts.
It also provides information about the total number of devices renamed as a result of the hack as well as the “Total devices forced to play video,” “Total Google Homes devices,” and “Total SmartTVs/Chromecast devices” that were breached. The hackers exploited the routers’ Universal Plug and Play (UPnP) option. Google has admitted to the hacks.

The website also had an FAQ section featuring questions like “What is going on?” “What information is being leaked?” and “What can hackers do with this?” HackerGiraffe and j3ws3r provided information to the people they hacked and gave advice about how they can best protect their devices in the future. The answer: “Disable UPnP on your router, and if you’re port forwarding ports 8008/8443/8009 then STOP forwarding them.”
The hackers informed those affected that they were able to wirelessly play media of their choice on users’ devices, erase Wi-Fi network setting, rename devices, and connect other devices wirelessly with Chromecast and Google Home. HackerGiraffe clarified that their intention wasn’t to cause real harm or steal data but to alert Google and its customers to the vulnerability.
HackerGiraffe further added that the attack doesn’t gather or save any information from affected devices.
Google told The Verge that many users reported: “an unauthorized video played on their TVs via a Chromecast device.” The company confirmed the hack was due to router settings. Both HackerGiraffe and Google told The Verge the best way to fix the issue is by turning off the Universal Plug and Play (UPnP) option on their routers.
Since the hacked seemed not to have any malicious purpose, it might be a blessing in disguise for some users who are now aware of a security loophole. This will prevent malicious actors from using it for much more nefarious deeds. Since HackerGiraffe gave a solution to the security bug, some may even find humor in the situation.
This isn’t the first time the hackers backed Kjellberg and promoted his YouTube channel. The duo admitted that they were behind the printer hacks that told users to subscribe to PewDiePie, back in November. HackerGirrafe gained access to close to 50,000 unsuspecting printers worldwide to promote PewDiePie and help him retain his position as the most subscribed YouTuber. At the time, he was facing tough competition from Indian music label T-Series’ YouTube channel.
Just last month, PewDiePie was at the center of another controversial hack orchestrated by his fans. This time they targeted The Wall Street Journal, which posted a story in 2017 about Kjellberg being anti-semitic after he had paid two strangers to hold up a sign reading “Death to all Jews” in a publicity stunt that lead Disney to cut all ties to the YouTube star. In response to the critical story, hackers replaced sponsored content on the website with calls for the newspaper to apologize for taking the stunt out of context.
Kjellberg is the most subscribed YouTuber, currently having a whopping 79 million subscribers. The Swedish star has successfully maintained his position as the most subscribed YouTuber since 2013.
It is highly impressive how many subscribers he gained after his “war” against the Indian music conglomerate, even adding a mind-blowing half million subscribers in one day back in October.
The YouTuber himself had nothing to do with any of the hacks as far as we know. They were all conducted by members of his enormous fan base.
It’s likely that the media will find a way to blame PewDiePie. He has made mistakes in the past, including his “all Jews must die” joke and saying the N-word during a live stream, for which he later apologized.
It will be interesting to see how this whole hacking fiasco turns out. It will be in everyone’s interest, PewDiePie’s included, to prevent further hacks in the future.





Share Your Thoughts