Hackers are injecting crypto-mining software in fake Adobe Flash updates
Hiding malware in Adobe flash updates is an old tactic. However, a researcher from cyber security company Palo Alto Networks reports signs of crypto-miner malware in the fake Adobe Flash updates. Palo Alto researcher said that the miners use your computer to expand their control over installing the affected update. The update package updates the plugin itself but also installs an illicit mining malware on your computer that eventually lowers your computer’s performance and uses it for mining purpose.
What’s happening?
These fakes are tricking users into installing Adobe Flash updates, and as soon as the user installs the update, the malware also gets installed on the computer. The update seems legitimate but is insidious.
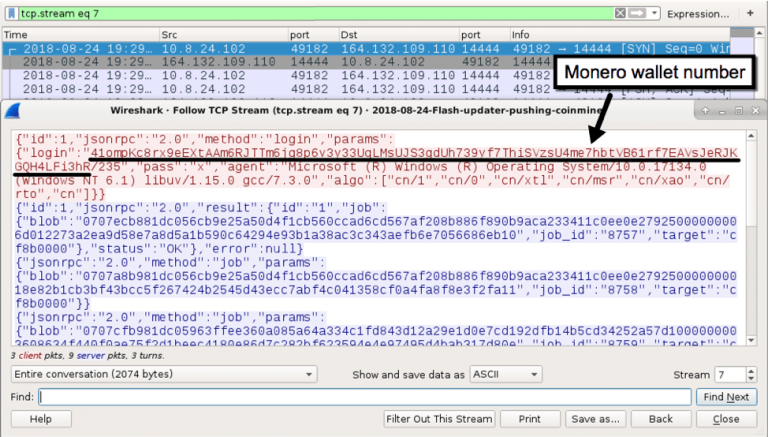
The researcher also reported that the hackers are more interested in Monero coin and are using illicit mining leaving no marks. Monero coin’s privacy protocol makes it extremely hard to trace, and hence it’s a win for malware injectors. The fake installers update the Adobe Flash plugin but also installs XMRig in the background. The program after getting installed on the victim’s computer uses graphics card and processing power to mine Monero coin without any notice.
Because of the legitimacy of the update, the victim may not notice anything about the malware. Meanwhile, the miner is quietly running in the background of the person’s Windows computer. It is a new type of deceptive attack where researcher noticed that the files they saw are starting with “AdobeFlashPlayer_ _” and are from non-Adobe servers. To keep a check on your downloads, you should know that these downloads always contain string “flashplayer_down.php?clickid=” in the URL of the download. Palo Alto researcher found almost 113 examples of this malware since March.
The malware attacks are reportedly a planned campaign. The distribution of these cryptocurrency minders is happening via the distribution of legitimate software updates. An educated user with a decent web filter installed can lower the risk of becoming a victim of these fake updates.
Let us know what do you think about this deception by hackers!
Share your thoughts in the comments below.